Однажды мне захотелось иметь своего скайп-бота, который мог бы форвардить мне сообщения из внешних источников.
В первой статье я расскажу как запустить linux-клиент скайпа на виртуальной машинке и научиться отправлять сообщения с консоли желаемому собеседнику. Как всегда, openvz-контейнер, 32бита, debian wheezy. Поехали!
# aptitude install x11vnc xfvb runit
# wget http://www.skype.com/go/getskype-linux-deb-32
# dpkg -i skype.deb
# aptitude install
The following actions will resolve these dependencies:
Remove the following packages:
1) skype
Accept this solution? [Y/n/q/?] n
The following actions will resolve these dependencies:
Install the following packages:
Все нужные пакеты, от которых зависит скайп будут установлены.
Далее займемся ранит-скриптами для запуска наших демонов.
Создадим скрипт для запуска виртуального X-сервера:
# mkdir -p /etc/sv/Xvfb/
# $EDITOR /etc/sv/Xvfb/run
Со следующим содержимым:
#!/bin/bash
exec 2>&1
exec Xvfb
Включим получившуюся службу runit:
# chmod a+x /etc/sv/Xvfb/run
# ln -s /etc/sv/Xvfb/ /etc/service/Xvfb
# sv status Xvfb
run: Xvfb: (pid 20111) 5s
Отлично, X-сервер запущен уже в течении 5 секунд, все идет по плану.
Продолжим, подготовим все для запуска скайп-бота:
# adduser skype
# aptitude install git python-setuptools python-dbus python-gobject dbus-x11
# git clone https://github.com/awahlig/skype4py.git
# cd skype4py
# python setup.py install
Если ошибок нет, продолжаем:
# export DISPLAY=":0"
# x11vnc &
# su - skype
Теперь создадим скрипты для управления скайпом.
sendim.py
# -*- coding: utf-8 -*-
import Skype4Py
import sys
# Create an instance of the Skype class.
skype = Skype4Py.Skype()
# Connect the Skype object to the Skype client.
skype.Attach()
user = sys.argv[1]
msg = ' '.join(sys.argv[2:])
message = skype.SendMessage(user, msg)
print sys.argv[1]
print sys.argv[2:]
sendim.sh
#!/bin/bash
export DISPLAY=:0
export VERSIONER_PYTHON_PREFER_32_BIT=yes
echo "$@" >> /tmp/sendimsh.log
python ~skype/sendim.py "$@"
Делаем его исполняемым и запускаем скайп:
# chmod a+x sendim.sh
# export DISPLAY=“:0”
# skype
Подключаемся внц-клиентом к своему серверу.
Идем на
https://login.skype.com/account/signup-form, регистрируем новый аккаунт для бота. Соглашаемся с лицензионным соглашением. Вводим логин и пароль, не забываем поставить галочку.
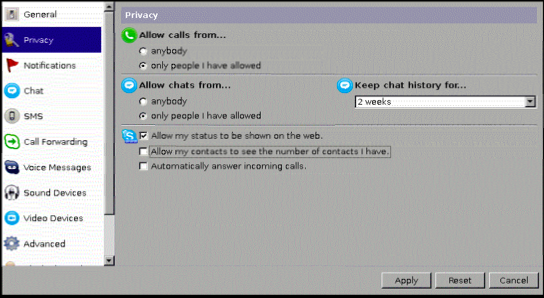
В настройках прайваси ставим устраивающие галки.
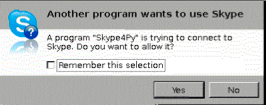
В соседнем окне терминала проверяем с помощью скрипта, должно выскочить уведомление о том что скайпом хочет управлять некая сила, соглашаемся, не забывая поставить галочку.
# su - skype
# sendim.sh skypename test
Теперь нам понадобится еще пара скриптов для отправки запросов авторизации контактам с консоли:
addcontact.py
# -*- coding: utf-8 -*-
import Skype4Py
import sys
# Create an instance of the Skype class.
skype = Skype4Py.Skype()
# Connect the Skype object to the Skype client.
skype.Attach()
#user = sys.argv[1]
#msg = ' '.join(sys.argv[2:])
#message = skype.SendMessage(user, msg)
print sys.argv[1]
print sys.argv[2:]
client = Skype4Py.client.Client(skype)
client.OpenAddContactDialog(sys.argv[1])
client.ButtonReleased(1)
addcontact.sh
#!/bin/bash
export DISPLAY=:0
export VERSIONER_PYTHON_PREFER_32_BIT=yes
echo "$@" >> /tmp/addcontact.log
python ~skype/addcontact.py "$1"
sleep 3
WID=$(xdotool search "Say hello to $1")
xdotool windowactivate $WID
xdotool key "0x020"
Соответсвенно понадобится еще один пакет, т.к. я ничего лучше не придумал, чем кликать по кнопке в интерфейсе. Для этого же понадобится оконный менеджер, т.к. без него xdotool не видит окон, я выбрал простецкий fluxbox:
# aptitude install xdotool fluxbox
Из-под рута создадим директорию под runit-службу fluxbox и скрипт для запуска. Сделаем исполняемым и активируем.
# mkdir /etc/sv/fluxbox
# $EDITOR /etc/sv/fluxbox/run
Со следующим содержимым:
#!/bin/bash
TIME="Finished. Process took %E. %P CPU was eaten. %MK memory was used." # time stuff
name=`basename $(dirname $(pwd)/fake)` # ugly hack
workingdir="/home/skype/"
command="su - skype -c /usr/bin/fluxbox -- --replace"
export DISPLAY=":0"
exec 2>&1
echo starting $name...
export TIME
set -x
cd $workingdir
exec chpst -v time $command
# chmod +x /etc/sv/fluxbox/run
# ln -s /etc/sv/fluxbox/ /etc/service/fluxbox
В окне внц-клиента должен появится оконный менеджер.
Из-под пользователя skype отправим запрос авторизации самому себе(skypename у нас будет testname):
# ./addcontact.sh testname
В окне внц-клиента можно наблюдать как появится окно запроса и потом нажмется кнопка отправки.
Авторизуем своего бота и пробуем что-нибудь себе отправить:
# ./sendim.sh testname "Ya tvoy sluga, ya tvoy rabotnik"
Должно придти сообщение.
В внц-клиенте выходим из скайпа. Остались финальные штришки - добавить скайп в автозапуск. И убедиться что виртуалка/контейнер переживает перезагрузку. Это будет домашним заданием.
А вот работающий скрипт для ранит-задания.
#!/bin/bash
TIME="Finished. Process took %E. %P CPU was eaten. %MK memory was used." # time stuff
name=`basename $(dirname $(pwd)/fake)` # ugly hack
workingdir="/home/skype/"
command="su - skype -c /usr/bin/skype"
export DISPLAY=":0"
exec 2>&1
echo starting $name...
export TIME
set -x
cd $workingdir
exec chpst -v time $command

 Now you need addition helper scripts for making authorization requests.
Now you need addition helper scripts for making authorization requests.